继续关于.htaccess相关知识的介绍,此为下一章节,本章节主要介绍一些常用的案例汇聚,关于验证测试.htaccess的知识点可以查看我上一章节的内容。
常用的.htaccess实用案例
忽略大小写拒绝所有以下后缀的访问
<FilesMatch "\.([Ll][Oo][Gg])|([eE][xX][eE])|([tT][xX][tT])$">
Order allow,deny
Deny from all
</FilesMatch>
<FilesMatch "^.*\.([Ll][Oo][Gg])|([eE][xX][eE])|([tT][xX][tT])">
Order allow,deny
Deny from all
</FilesMatch>
过时写法,但可使用
<Files ~ "^.*\.([Ll][Oo][Gg])|([eE][xX][eE])|([tT][xX][tT])">
Order allow,deny
Deny from all
Satisfy All
</Files>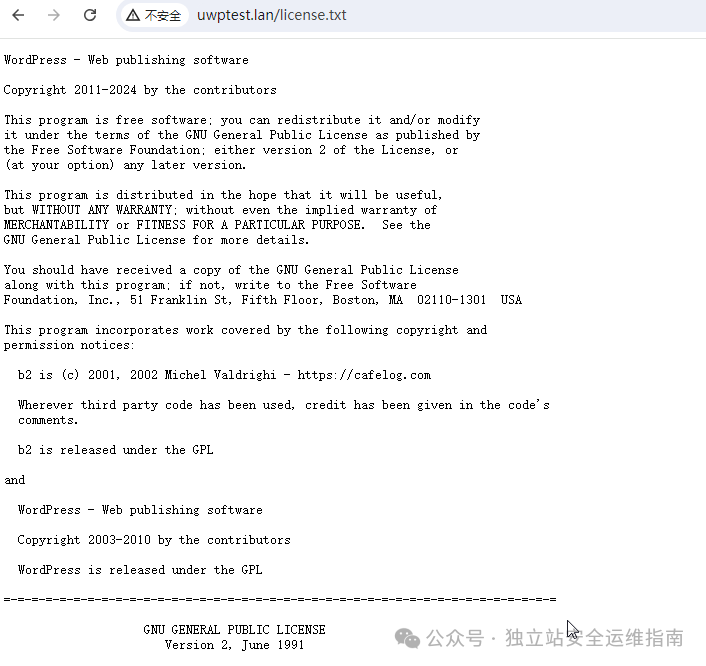
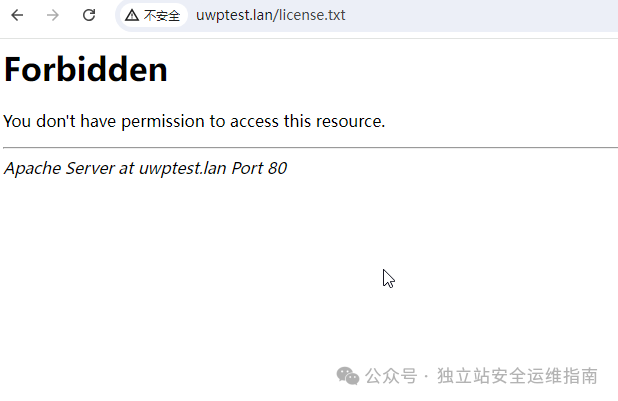

防护.htaccess文件被访问
<FilesMatch "^.*\.([Hh][Tt][Aa])">
Order allow,deny
Deny from all
</FilesMatch>
或者
<Files ~ "^.*\.([Hh][Tt][Aa])">
Order allow,deny
Deny from all
Satisfy all
</Files>防止wp-config.php文件被访问
<Files wp-config.php>
Order allow,deny
Deny from all
</Files>防止XML-RPC DDoS攻击
<FilesMatch "^(xmlrpc\.php)">
Order deny,allow
Deny from all
</FilesMatch>
或者
<FilesMatch "^(xmlrpc\.php)">
Order allow,deny
Deny from all
</FilesMatch>设置网站后台白名单
设置网站后台白名单,需要在wp-admin目录下新建.htaccess写入下面指令
AuthUserFile /dev/null
AuthGroupFile /dev/null
AuthName "WordPress Admin Access Control"
AuthType Basic
<LIMIT GET>
Order deny,allow
Allow from 10.10.9.232
Deny from all
</LIMIT>
另一种白名单设置方式
<Limit GET POST>
Order allow,deny
deny from 10.10.9.232
</Limit>
Allow from all网站防盗链
RewriteEngine on
RewriteCond %{HTTP_REFERER} !^$
RewriteCond %{HTTP_REFERER} !^http(s)?://(www\.)?uwptest.lan [NC]
RewriteRule \.(jpe?g?|png|gif|ico|pdf|flv|swf|gz)$ - [NC,F,L]
测试验证方式:
curl -I -e "http://hehe.com" http://uwptest.lan/wp-content/themes/twentytwentythree/screenshot.png针对插件和主题目录下的文件进行防护(PHP文件访问限制)
RewriteCond %{REQUEST_URI} !^/wp-content/plugins/file/to/exclude\.php
RewriteCond %{REQUEST_URI} !^/wp-content/plugins/directory/to/exclude/
RewriteRule wp-content/plugins/(.*\.php)$ - [R=404,L]
RewriteCond %{REQUEST_URI} !^/wp-content/themes/file/to/exclude\.php
RewriteCond %{REQUEST_URI} !^/wp-content/themes/directory/to/exclude/
RewriteRule wp-content/themes/(.*\.php)$ - [R=404,L]
上面提到的插件和主题目录下文件名都需要根据实际情况更改为自己适用的。针对wp-content进行防护
Order deny,allow
Deny from all
<Files ~ ".(xml|css|jpe?g|png|gif|js)$">
Allow from all
</Files>
上述需要在wp-content目录下新建.htaccess文件,然后将上述代码贴进去针对wp-include进行防护
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ - [F,L]
RewriteRule !^wp-includes/ - [S=3]
RewriteRule ^wp-includes/[^/]+\.php$ - [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php - [F,L]
RewriteRule ^wp-includes/theme-compat/ - [F,L]
</IfModule>
上述需要在wp-include目录下新建.htaccess文件,然后将上述代码贴进去禁用特定目录下的PHP执行
<Directory "/var/www/wp-content/uploads/">
<Files "*.php">
Order Deny,Allow
Deny from All
</Files>
</Directory>脚本注入攻击防护
Options +FollowSymLinks
RewriteEngine On
RewriteCond %{QUERY_STRING} (<|%3C).*script.*(>|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|[|%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|[|%[0-9A-Z]{0,2})
RewriteRule ^(.*)$ index.php [F,L]禁止目录浏览
Options All -Indexes启用Gzip压缩
<IfModule mod_deflate.c>
Compress HTML, CSS, JavaScript, Text, XML and fonts
AddOutputFilterByType DEFLATE application/javascript
AddOutputFilterByType DEFLATE application/rss+xml
AddOutputFilterByType DEFLATE application/vnd.ms-fontobject
AddOutputFilterByType DEFLATE application/x-font
AddOutputFilterByType DEFLATE application/x-font-opentype
AddOutputFilterByType DEFLATE application/x-font-otf
AddOutputFilterByType DEFLATE application/x-font-truetype
AddOutputFilterByType DEFLATE application/x-font-ttf
AddOutputFilterByType DEFLATE application/x-javascript
AddOutputFilterByType DEFLATE application/xhtml+xml
AddOutputFilterByType DEFLATE application/xml
AddOutputFilterByType DEFLATE font/opentype
AddOutputFilterByType DEFLATE font/otf
AddOutputFilterByType DEFLATE font/ttf
AddOutputFilterByType DEFLATE image/svg+xml
AddOutputFilterByType DEFLATE image/x-icon
AddOutputFilterByType DEFLATE text/css
AddOutputFilterByType DEFLATE text/html
AddOutputFilterByType DEFLATE text/javascript
AddOutputFilterByType DEFLATE text/plain
AddOutputFilterByType DEFLATE text/xml
Remove browser bugs (only needed for really old browsers)
BrowserMatch ^Mozilla/4 gzip-only-text/html
BrowserMatch ^Mozilla/4\.0[678] no-gzip
BrowserMatch \bMSIE !no-gzip !gzip-only-text/html
Header append Vary User-Agent
</IfModule>设置永久重定向
Redirect 301 /sample-page/ http://uwptest.lan/hello-world/只更换新旧域名,原始URI地址不变
RewriteEngine On
RewriteCond %{HTTP_HOST} ^xxxwebhostings\.com [NC,OR]
RewriteCond %{HTTP_HOST} ^www\.xxxwebhostings\.com [NC]
RewriteRule ^(.*)$ https://ditigalocean.com/$1 [L,R=301,NC]
或者
RewriteEngine On
RewriteCond %{HTTP_HOST} !^www\.xxxcheapwebhosting\.com$
RewriteRule (.*) http://www.ditigalocean.com/$1 [R=301,L]
RewriteCond %{HTTP_HOST} !^xxxcheapwebhosting\. com$
RewriteRule (.*) http://www.ditigalocean.com/$1 [R=301,L]将旧域名所有可能性URL地址强制跳转到新的根域名,不带任何URL地址
RewriteCond %{HTTP_HOST} ^xxlegs\.com\/.*$ [NC,OR]
RewriteCond %{HTTP_HOST} ^www\.xxlegs\.com\/.*$ [NC]
RedirectMatch 301 ^/(.*)$ https://www.ditigalocean.com/重定向到non-www
RewriteEngine on
RewriteCond %{HTTP_HOST} ^www\.(.*)$ [NC]
RewriteRule ^(.*)$ https://%1/$1 [R=301,L]
RewriteCond %{HTTPS} !on
RewriteRule (.*) https://%{HTTP_HOST}%{REQUEST_URI} [R=301,L]重定向到www
RewriteEngine on
RewriteCond %{HTTPS} !on [OR]
RewriteCond %{HTTP_HOST} !^www\.
RewriteRule (.*) https://www.xxxxx.com%{REQUEST_URI} [L,R=301]将来访者重定向到一个维护页面
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{REMOTE_ADDR} !^62\.234\.12\.45
RewriteCond %{REQUEST_URI} !/maintenance.html$ [NC]
RewriteCond %{REQUEST_URI} !\.(jpe?g?|png|gif) [NC]
RewriteRule .* /maintenance.html [R=503,L]
</IfModule>限制对wp-includes目录下的所有文件访问
<IfModule mod_rewrite.c>
RewriteEngine On
RewriteBase /
RewriteRule ^wp-admin/includes/ - [F,L]
RewriteRule !^wp-includes/ - [S=3]
RewriteRule ^wp-includes/[^/]+\.php$ - [F,L]
RewriteRule ^wp-includes/js/tinymce/langs/.+\.php - [F,L]
RewriteRule ^wp-includes/theme-compat/ - [F,L]
</IfModule>拦截XSS攻击
<IfModule mod_rewrite.c>
RewriteCond %{QUERY_STRING} (\|%3E) [NC,OR]
RewriteCond %{QUERY_STRING} GLOBALS(=|\[|\%[0-9A-Z]{0,2}) [OR]
RewriteCond %{QUERY_STRING} _REQUEST(=|\[|\%[0-9A-Z]{0,2})
RewriteRule .* index.php [F,L]
</IfModule>启用浏览器缓存
<IfModule mod_expires.c>
ExpiresActive On
ExpiresByType image/jpg "access 1 year"
ExpiresByType image/jpeg "access 1 year"
ExpiresByType image/gif "access 1 year"
ExpiresByType image/png "access 1 year"
ExpiresByType text/css "access 1 month"
ExpiresByType application/pdf "access 1 month"
ExpiresByType text/x-javascript "access 1 month"
ExpiresByType application/x-shockwave-flash "access 1 month"
ExpiresByType image/x-icon "access 1 year"
ExpiresDefault "access 2 days"
</IfModule>设置自定义错误页面
<Files xmlrpc.php>
Order allow,deny
Deny from 10.10.9.232
Allow from all
</Files>
ErrorDocument 403 /403.html
上述是当被拦截时,显示系统默认403页面,重定向到自定义的403.html
下面这个同理,可以自己定义一个404页面,然后根据404重定向过去。
ErrorDocument 404 /404.html强制跳转HTTPS
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]
或者
RewriteEngine On
RewriteCond %{HTTPS} off
RewriteRule ^(.*)$ https://%{SERVER_NAME}%{REQUEST_URI} [L,R=301]强制跳转HTTP
RewriteEngine On
RewriteCond %{HTTPS} on
RewriteRule ^ http://%{HTTP_HOST}%{REQUEST_URI} [L,R=301]删除博客中的category
RewriteRule ^category/(.+)$ http://uwptest.lan/$1 [R=301,L]压缩静态数据
AddOutputFilterByType DEFLATE text/html text/plain text/xml application/xml application/xhtml+xml text/javascript text/css application/x-javascript
BrowserMatch ^Mozilla/4 gzip-only-text/html
BrowserMatch ^Mozilla/4.0[678] no-gzip
BrowserMatch bMSIE !no-gzip !gzip-only-text/html拒绝网页链接评论
RewriteEngine On
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{REQUEST_URI} .wp-comments-post\.php*
RewriteCond %{HTTP_REFERER} !.*yourblog.com.* [OR]
RewriteCond %{HTTP_USER_AGENT} ^$
RewriteRule (.*) ^http://%{REMOTE_ADDR}/$ [R=301,L]根据浏览器语言跳转不同的页面
RewriteCond %{HTTP:Accept-Language} ^zh-cn.*$ [NC]
RewriteRule ^/?$ index_cn.htm [R=301,L]WordPress后台加一个401认证
<Files /wp-admin>
AuthName "Admins Only"
AuthType Basic
AuthUserFile /home/admin/.htpasswds/public_html/wp-admin/passwd
Require valid-user
</Files>
或者
AuthName ""
AuthUserFile /home/admin/.htpasswds/public_html/wp-admin/passwd
AuthGroupFile /dev/null
AuthType basic
require user put your username here
<Files admin-ajax.php>
Order allow,deny
Allow from all
Satisfy any
</Files>
若是VPS搭建的WordPress,有root权限,可以自己根据下面具体步骤操作,下面是在Rocky Linux 9.4上检验可用
sudo mkdir /var/www/html/private
sudo vim /etc/httpd/conf.d/private.conf
<Directory "/var/www/html/private">
AllowOverride Authconfig
</Directory>
sudo apachectl configtest
sudo vim /var/www/html/private/.htaccess
AuthType Basic
AuthName "Enter your credentials: "
AuthUserFile "/etc/httpd/conf/.userdb"
Require user user1
sudo vim /var/www/html/private/index.html
Private Index File
sudo chown -R apache:apache /var/www/html/private
sudo chown -R 770 /var/www/html/private
cd /etc/httpd/conf/
sudo htpasswd -c .userdb user1
这里回车后输入密码
sudo chown apache:apache .userdb
sudo chmod 660 .userdb
sudo apachectl graceful 这条命令作用是重载配置文件并正常重启
firefox --private-window rhhost1.localnet.com/private拦截针对WordPress作者信息进行暴力破解扫描
RewriteEngine On
RewriteBase /
RewriteCond %{QUERY_STRING} (author=\d+) [NC]
RewriteRule .* - [F]设置WordPress管理后台仅允许白名单IP访问
ErrorDocument 401 /path-to-your-site/index.php?error=404
ErrorDocument 403 /path-to-your-site/index.php?error=404
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
RewriteCond %{REMOTE_ADDR} !^IP Address One$
RewriteCond %{REMOTE_ADDR} !^IP Address Two$
RewriteCond %{REMOTE_ADDR} !^IP Address Three$
RewriteRule ^(.*)$ - [R=403,L]
</IfModule>
或者
ErrorDocument 401 /path-to-your-site/index.php?error=404
ErrorDocument 403 /path-to-your-site/index.php?error=404
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{REQUEST_METHOD} POST
RewriteCond %{HTTP_REFERER} !^http://(.*)?your-site.com [NC]
RewriteCond %{REQUEST_URI} ^(.*)?wp-login\.php(.*)$ [OR]
RewriteCond %{REQUEST_URI} ^(.*)?wp-admin$
RewriteRule ^(.*)$ - [F]
</IfModule>禁用访问特定文件
<FilesMatch "^.*(error_log|wp-config\.php|php.ini|\.[hH][tT][aApP].*)$">
Order deny,allow
Deny from all
</FilesMatch>重定向的方式
Redirect 301 / http://www.mynewwebsite.com/
Redirect 301 /[old_permalink].html [website_URL]/[current_permalink].html
Redirect 302 /[old_permalink].html [website_URL]/[current_permalink].html域名重定向到子目录
RewriteCond %{HTTP_HOST} ^example.com$
RewriteCond %{REQUEST_URI} !^/sub-directory-name/
RewriteRule (.*) /subdir/$1在线.htaccess工具
- .htaccess Generator
- Test your htaccess rewrite rules
- Htaccess Builder
- .htaccessEditor
- .Mod Rewrite Generator
推荐.htaccess插件
总结
关于.htacces相关的案例差不多介绍完成了,上面给出的案例大部分我都经过验证测试可用,其中一部分是摘自互联网需要大家自行验证测试。